Frequently Asked Questions
Sometimes it is due to a spelling mistake when registering your e-mail address.Please check your e-mail address is correct. If it is incorrect, complete the registration process again.
Step1
Click on claim coupon
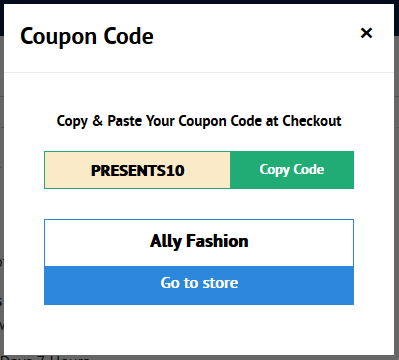
Step2
Click on copy code
Step3
The code will now show that it has been copied
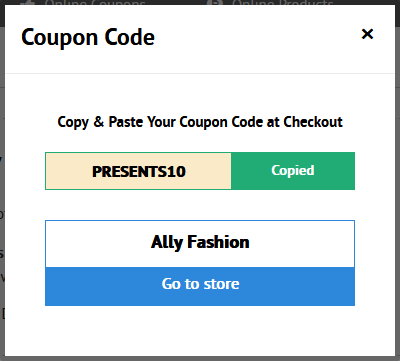
Click on go to store. You will now be transferred to the store
Step4
Once you have registered an account and progressed to the checkout, click on discount code, apply coupon or promotional code. Each store will have a different description for the code.

Step5
Paste or type in the coupon code then click on apply.

Step6
Then click on apply.
The Woolworths WISH gift cards can be used at all stores that are owned by Woolworths click here to see a list of the participating stores.
We only stock e-gift cards and we do not stock physical gift cards.
Your Woolworths WISH e-gift card can be used online. To use the card online, copy and paste the online number and your pin number on your e-gift card when completing the checkout process.
When you using your Woolworths e-gift card in store simply mention at the point of sale that you are paying using an e-gift card, then type in the in the card number and the pin number and the amount of your purchase will be debited from your card.
The e-gift card will be emailed to you. The e-gift cards can be stored on your phone, or you can print out the e-gift and take it into the store. Alternatively, you can take a photo of the card and store it on your phone.
All you need to redeem your e-gift card is the card number and the pin number.
The Coles e-gift cards can only be used at Coles Supermarkets and only in-store.
The Coles e-gift cards cannot be used online.
Your Coles e-gift card will be emailed to you. The e-gift cards can be stored on your phone, or you print out the e-gift and take it to the store.
When you are in the store, simply scan the barcode at the point of sale and type in the pin number.
Your e-gift will be sent to you as a link, simply hover your mouse over the link and left click on the mouse button.
It may also require you to press control (Ctrl) on the keyboard then left click on the mouse.
Payment for the e-gift cards is by Mastercard or Visa card. We do not accept American Express.
After the payment is received and cleared, your e-gift card will be emailed to you within 24 hours.
It is generally within 24 hours of payment being received.
If you have an existing purchase history with us the timeframe may be reduced.
No you don't need a gift card to shop online, all you need to do is log in through the website where you will be redirected to the store of your choice.
Some of the e-gift cards can be used online.
The Woolworths WISH e-gift card can be used at Dan Murphy's, BWS and Cellarmasters.
There is nothing that you have do when shopping through the site to ensure that your purchase is helping to support the charities.
Just log in before you click on go to store. There is a tracking code in the URL when you are being transferred to the shop which will link your donation back to the charities you are supporting.
If you have a problem with your order through any of the online shops or local shops you will need to contact the shop directly. We are purely a referrer to the shops and your order and purchase is directly with the shop itself.
If you have any questions with the e-gift-card please fill out the customer support form at the bottom of the website. Please do not contact our organisation direct as we will not be able to assist and will refer you back to customer support.
